dig
-
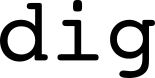
Used for: Finding information on domain names.
dig man page: http://bit.ly/2suSFzuNotes:
- Other tools in this area of Berkeley Internet Name Domain (BIND) are host, nslookup
- List of DNS record types: https://en.wikipedia.org/wiki/List_of_DNS_record_types
Perform a dig query.
$ dig www.hp.com ; <<>> DiG 9.9.4-RedHat-9.9.4-37.el7 <<>> www.hp.com ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 14555 ;; flags: qr rd ra; QUERY: 1, ANSWER: 3, AUTHORITY: 7, ADDITIONAL: 9 ;; OPT PSEUDOSECTION: ; EDNS: version: 0, flags:; udp: 4096 ;; QUESTION SECTION: ;www.hp.com. IN A ;; ANSWER SECTION: www.hp.com. 1753 IN CNAME www.hpgtm.nsatc.net. www.hpgtm.nsatc.net. 120 IN A 15.240.238.60 www.hpgtm.nsatc.net. 120 IN A 15.201.49.153 ;; AUTHORITY SECTION: nsatc.NET. 40692 IN NS l.ns.nsatc.net. nsatc.NET. 40692 IN NS d.ns.nsatc.net. nsatc.NET. 40692 IN NS g.ns.nsatc.net. nsatc.NET. 40692 IN NS e.ns.nsatc.net. nsatc.NET. 40692 IN NS c.ns.nsatc.net. nsatc.NET. 40692 IN NS a.ns.nsatc.net. nsatc.NET. 40692 IN NS b.ns.nsatc.net. ;; ADDITIONAL SECTION: a.ns.nsatc.NET. 40692 IN A 8.26.215.27 b.ns.nsatc.NET. 40692 IN A 8.254.92.155 b.ns.nsatc.NET. 40692 IN A 198.78.208.155 c.ns.nsatc.NET. 40692 IN A 8.26.204.25 d.ns.nsatc.NET. 40692 IN A 4.27.16.155 e.ns.nsatc.NET. 40692 IN A 4.26.227.27 g.ns.nsatc.NET. 40692 IN A 205.128.88.25 l.ns.nsatc.NET. 40692 IN A 8.26.197.27 ;; Query time: 164 msec ;; SERVER: 10.211.55.1#53(10.211.55.1) ;; WHEN: Sun Jul 02 10:58:15 BST 2017 ;; MSG SIZE rcvd: 373Breaking it down, what does that output tell you?
This part tells you what options you passed to dig, what version, a summary & what global options are set
; <<>> DiG 9.9.4-RedHat-9.9.4-37.el7 <<>> www.hp.com ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 14555 ;; flags: qr rd ra; QUERY: 1, ANSWER: 3, AUTHORITY: 7, ADDITIONAL: 9This part tells you any additional options and the questions section is what you asked dig to do.
;; OPT PSEUDOSECTION: ; EDNS: version: 0, flags:; udp: 4096 ;; QUESTION SECTION: ;www.hp.com. IN AThis part gives you the results of what you asked dig to do.
;; ANSWER SECTION: www.hp.com. 1753 IN CNAME www.hpgtm.nsatc.net. www.hpgtm.nsatc.net. 120 IN A 15.240.238.60 www.hpgtm.nsatc.net. 120 IN A 15.201.49.153The authorities section, tells you that these servers will give an the authoritative answer for your query.
;; AUTHORITY SECTION: nsatc.NET. 40692 IN NS l.ns.nsatc.net. nsatc.NET. 40692 IN NS d.ns.nsatc.net. nsatc.NET. 40692 IN NS g.ns.nsatc.net. nsatc.NET. 40692 IN NS e.ns.nsatc.net. nsatc.NET. 40692 IN NS c.ns.nsatc.net. nsatc.NET. 40692 IN NS a.ns.nsatc.net. nsatc.NET. 40692 IN NS b.ns.nsatc.net.The additional section tells you the IP addresses of the previous authority section.
Do a short lookup rather than the lengthy output.
$ dig www.hp.com +short www.hpgtm.nsatc.net. 15.240.238.62 15.217.49.156Get the A records (the address record) from your query, with the option +noall, do not display everything, just the +answers section.
$ dig www.hp.com A +noall +answer ; <<>> DiG 9.9.4-RedHat-9.9.4-37.el7 <<>> www.hp.com A +noall +answer ;; global options: +cmd www.hp.com. 3549 IN CNAME www.hpgtm.nsatc.net. www.hpgtm.nsatc.NET. 69 IN A 15.201.49.155 www.hpgtm.nsatc.NET. 69 IN A 15.201.49.156Get the mail exchange record (MX). Does not have to be uppercase in the command.
$ dig hp.com mx +noall +answer ; <<>> DiG 9.9.4-RedHat-9.9.4-37.el7 <<>> hp.com mx +noall +answer ;; global options: +cmd hp.com. 3592 IN MX 10 smtp.hp.com.You can run the previous command for NS (Nameserver Record), ANY record, and A.
Run a trace on a query.
$ dig hp.com mx +traceSOA - Start of authority record:
$ dig hp.com soa +noall +answer ; <<>> DiG 9.9.4-RedHat-9.9.4-37.el7 <<>> hp.com soa +noall +answer ;; global options: +cmd hp.com. 3600 IN SOA txe01hpiibpe.ams.hp.net. hostmaster.hp.com. 443243001 3600 3600 2419200 900eg:
nsatc.net. 883 IN SOA admin.nsatc.net. dns.level3.net. 1497384039 10800 2700 3600000 900Contains the following information:
- The primary name server for the domain.
admin.nsatc.net. - The responsible party for the domain.
dns.level3.net. - A timestamp that changes whenever you update your domain.
1497384039 - The number of seconds before the zone should be refreshed.
10800 - The number of seconds before a failed refresh should be retried.
2700 - The upper limit in seconds before a zone is considered no longer authoritative.
3600000 - The negative result TTL (for example, how long a resolver should consider a negative result for a subdomain to be valid before retrying).
900
© Lightnetics 2024